CMMC 2.0 maintains the goal of safeguarding sensitive information
On November 04, 2021, the Department of Defense (DoD) announced CMMC 2.0 as the updated strategic direction of the CMMC program, based on an internal assessment by senior DoD leaders.
CMMC 2.0 is described as an enhanced program that maintains the goal of safeguarding sensitive information while simplifying the standard and improving the clarity of requirements.
Read the full text of the announcement here:
What has changed?
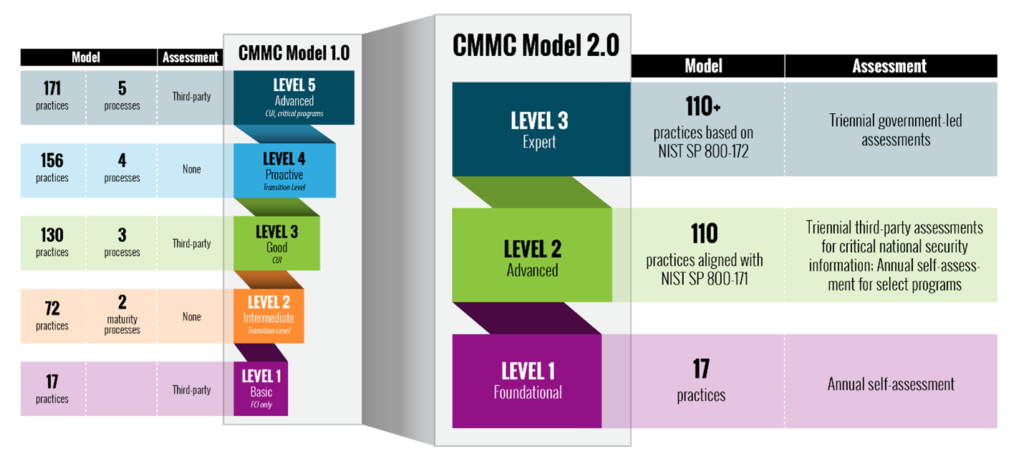
CMMC 1.0 established five levels for certification, ranging from “Level 1 Basic” with 17 practices necessary for “Basic cyber hygiene”, to “Level 5 Advanced” with 171 practices and 5 maturity processes required to protect Controlled Unclassified Information (CUI) in the most critical programs. CMMC 1.0 required certification through assessment by third party assessors for all Levels.
CMMC 2.0 reduces the number of levels to three, limits the practices to the 110 required in NIST 800-171, and eliminates the maturity processes entirely. Requirements for third party assessments are significantly reduced in CMMC 2.0. All Level 1 organizations will be able to demonstrate compliance through annual self-assessments, as will a portion of Level 2 organizations. Level 2 organizations involved with “critical national security information” will still be subject to triennial third party assessments. Level 3 organizations will require triennial, government-led assessments.
KEY FEATURES OF CMMC 2.0
Reduced requirements for assessment by certified third-party Assessors:
Allowing all Level 1 and some Level 2 organizations to self-assess will reduce assessment costs for those organizations. However, this change carries the same risk regarding the reliability of self-assessments as the DFARS requirements prior to CMMC. CMMC 2.0 adds a requirement for annual attestation by a senior company official that the company has met all requirements.
Allowance for some open items on the organization’s Plan of Action & Milestones:
For those Level 2 organizations where third-party assessments are required, CMMC 2.0 will allow certification with a limited number of open items on the organization’s Plan of Action & Milestones (POAM). It is expected that allowable open items will be limited to some of the less critical practices, and there will be a maximum period allowed to close those items, most likely no more than 180 days. This is a significant departure from CMMC 1.0 where there was no allowance for any open POAM actions whatsoever.
These changes will be implemented through the government’s rulemaking process which could take up to 24 months.
Here is the full text of the DoD announcement regarding the changes: https://www.acq.osd.mil/cmmc/index.html
NEXT STEPS
Companies should continue their cybersecurity efforts.
- NIST 800-171 requirements are unchanged. This means no change in requirements for Level 1, and slightly reduced requirements for Level 2.
- Removing the CMMC 1.0 “Maturity Processes” from the requirements reduces the requirements for specific documents, however NIST 800-171 Appendix E specifies requirements for “Policy and Procedures”.
- Companies handling CUI (Level 2) should prepare for third-party assessment. There is currently no way to know what will be considered “critical national security information.”
- Full implementation of CMMC 2.0 will be after the DoD’s rulemaking process and could take 24 months.
- Additional guidance for the interim, such as more clarity regarding allowable POAM items, is expected in the next 30-60 days.
- Contact Mark Sewell, Senior Consultant, Manufacturing at msewell@catalystconnection.org or 412.480.7862 for additional information.